Password Vulnerabilities can compromise the security of the system and pose a huge risk. Brute force attacks aiming to guess passwords are so common and can be easily used. Password-less Authentication mechanisms are methods of accessing systems or services without the need for traditional password-based authentication. Following are few commonly used methods
- SSH Keys: Secure Shell (SSH) keys are cryptographic keys used for authentication instead of passwords when connecting to SSH servers.
- Biometric Authentication: Biometric authentication uses unique biological characteristics (fingerprint, iris scan, face recognition, etc.) to verify a user’s identity.
- Single Sign On SSO solutions authenticate users across multiple applications or services using a single set of credentials.
- One-Time Passwords: OTPs are temporary authentication tokens sent via email or SMS to users’ registered devices.
- Device-based Authentication: Trusted devices, such as mobile phones or hardware tokens, can act as a form of authentication
In this article, I want to get into details of how SSH Keys work as authentication parameters. SSH stands for Secure Shell and is a network protocol to access network services on remote systems over an unsecured network[read Internet]. SSH follows client-server model and is a layer 7 protocol. Three Main aspects of SSH are
- Connection Establishment: This is the main part of the TCP connection establishment between the SSH client and the SSH server.
- Key Exchange and Encryption: The idea of Secure Shell Protocol is to have the data transmission secured over an unsecured network. Based on the algorithm agreed upon, data will be encrypted and decrypted accordingly.
- User Authentication: This can be Password-based or SSH Key based Authentication.
User Authentication using SSH Keys:
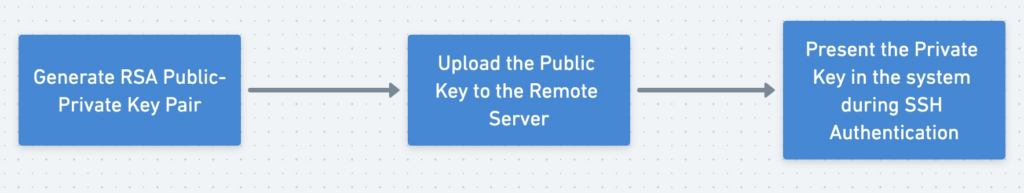
Steps involved in SSH Authentication:
- The client initiates the SSH Connection to the remote server.
- During the Key Exchange and Encryption Step, the client and server negotiate the cryptographic parameters, including the algorithms to be used for encryption, integrity, and key exchange. Session Keys will also be generated during this phase.
- The client sends the Key ID[like a username] to the remote server. This is the first step of Authentication
- The server checks its key database to see if there is a corresponding public key.
- The server generates a random number, encrypts it with the public key, and sends it to the client.
- The client decrypts the message with the private key and, along with the help of session keys, calculates the MD5 hash value of the message.
- The client then encrypts the hash value and sends it to the server.
- The server also calculates the MD5 hash value of the message sent to the client (with the help of session keys). If these two values match, that proves that the client possesses the corresponding private key, and the client is authenticated on the server.
Example of Key based Authentication with Linode Instance:
1. Generate the RSA Public and Private Key Pair:
[~]$:ssh-keygen -t rsa -b 2048 -C "`whoami`-linode-`date +%Y-%m-%d`" -f /Users/apadmana/Achuth/General/SSH/`whoami`-linode
Generating public/private rsa key pair.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /Users/apadmana/Achuth/General/SSH/apadmana-linode
Your public key has been saved in /Users/apadmana/Achuth/General/SSH/apadmana-linode.pub
The key fingerprint is:
SHA256:1Vr0wbkn2eLM1Wx/X6J8yO7kVD1ijCDhZFwpZD6T5Sg apadmana-linode-2023-11-30
The key's randomart image is:
+---[RSA 2048]----+
| o*.o. .... |
| *o*. o .o. |
| E O.o. o .=.|
| . +..oo =.B|
| S .. B.Bo|
| ..* =|
| ooo .+|
| += . .|
| o+. |
+----[SHA256]-----+
You have new mail in /var/mail/apadmana
[~]$:
[~]$:cat /Users/apadmana/Achuth/General/SSH/apadmana-linode.pub
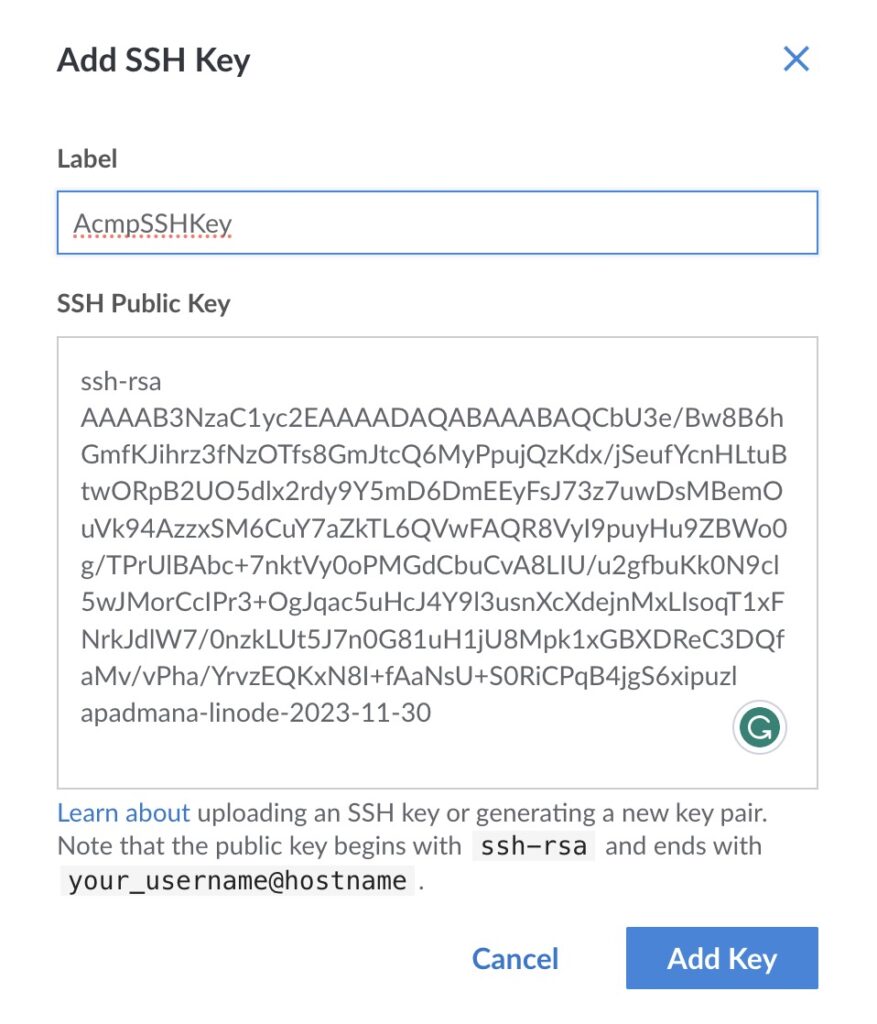
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCbU3e/Bw8B6hGmfKJihrz3fNzOTfs8GmJtcQ6MyPpujQzKdx/jSeufYcnHLtuBtwORpB2UO5dlx2rdy9Y5mD6DmEEyFsJ73z7uwDsMBemOuVk94AzzxSM6CuY7aZkTL6QVwFAQR8VyI9puyHu9ZBWo0g/TPrUlBAbc+7nktVy0oPMGdCbuCvA8LIU/u2gfbuKk0N9cl5wJMorCcIPr3+OgJqac5uHcJ4Y9l3usnXcXdejnMxLIsoqT1xFNrkJdlW7/0nzkLUt5J7n0G81uH1jU8Mpk1xGBXDReC3DQfaMv/vPha/YrvzEQKxN8I+fAaNsU+S0RiCPqB4jgS6xipuzl apadmana-linode-2023-11-30
[~]$:
2. Upload the Public Key to the Server. You can login to cloud.linode.com and try creating a new VM instance.
3. Present the Private Key while login
[~]$:ssh -i /Users/apadmana/Achuth/General/SSH/apadmana-linode root@172.105.63.162
The authenticity of host '172.105.63.162 (172.105.63.162)' can't be established.
ED25519 key fingerprint is SHA256:IgMxDDtn+EA5Cx3pgYcMGiv0cZ5uyl+7i6h9VNztXPg.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '172.105.63.162' (ED25519) to the list of known hosts.
Linux localhost 5.10.0-26-amd64 #1 SMP Debian 5.10.197-1 (2023-09-29) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
root@localhost:~#
root@localhost:~#
4. To understand what happened behind the scenes in step 3 ! Try the same command in debug mode with -v option.
[~]$:ssh -i /Users/apadmana/Achuth/General/SSH/apadmana-linode root@172.105.63.162 -v