Concepts:
Certificate Revocation: Certificate revocation is the act of invalidating a TLS/SSL before its scheduled expiration date. A certificate should be revoked immediately when its private key shows signs of being compromised or when the domain for which it was issued is no longer operational.
Certificate Revocation List: Certificates that are revoked are stored on a list by the CA, called the Certificate Revocation List(CRL).
Problem Statement :
When a client attempts to initiate a connection with a server, it checks for problems in the certificate, and part of this check is to ensure that the certificate is not on the CRL. CRLs may be exhaustive, and the client that conducts the check has to parse the whole list to find (or not find) the requested site’s certificate. This results in a lot of overhead and time. In such a scenario the client might unknowingly accept the revoked certificate.
Solution:
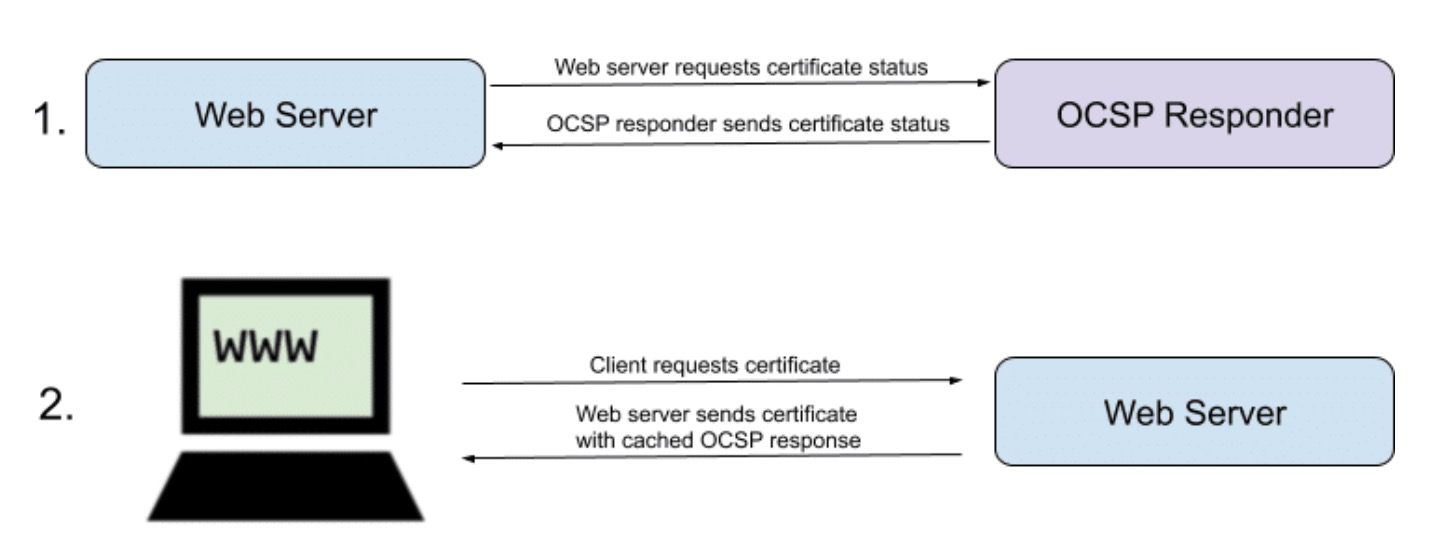
OSCP Stands for Online Certificate Status Protocol (OCSP). When the client wants to check the validity of the certificate, an OCSP request is sent to an OCSP Responder. This checks the specific certificate with a trusted certificate authority and an OCSP response is sent back with a response of either ‘good’, ‘revoked’, or ‘unknown’. OCSP responder = OCSP server. An OCSP server belongs to the CA that issued the digital certificate.
OSCP Stapling :
Problem Statement:
Unfortunately, OCSP came with a number of issues. Many OCSP implementations weren’t reliable enough, which pushed impatient browsers and other client software to implement OCSP checking in soft-fail mode. This means that if an OCSP server couldn’t be reached in time while responding, the certificate would be considered valid and they would proceed with the HTTPS connection.
Man-in-the-middle attacks have exploited this by blocking all OCSP queries or connections, using a stolen certificate[say when the Private Key has also been stolen] to gain access to a trusted HTTPS connection. This could result in sensitive information being shared with bad actors, which led to OCSP Stapling as a solution.
OSCP Stapling:
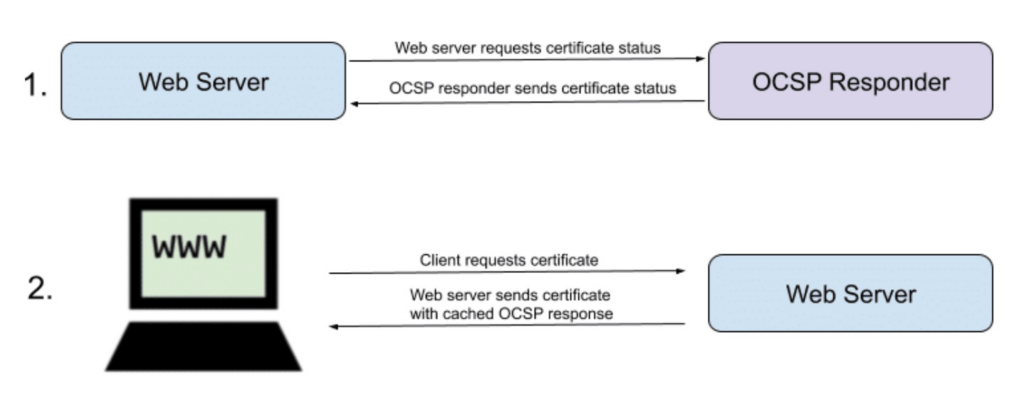
OCSP Must-Staple requires OCSP Stapling for the certificate. If a browser comes into contact with a certificate without OCSP Stapling, it will be rejected.